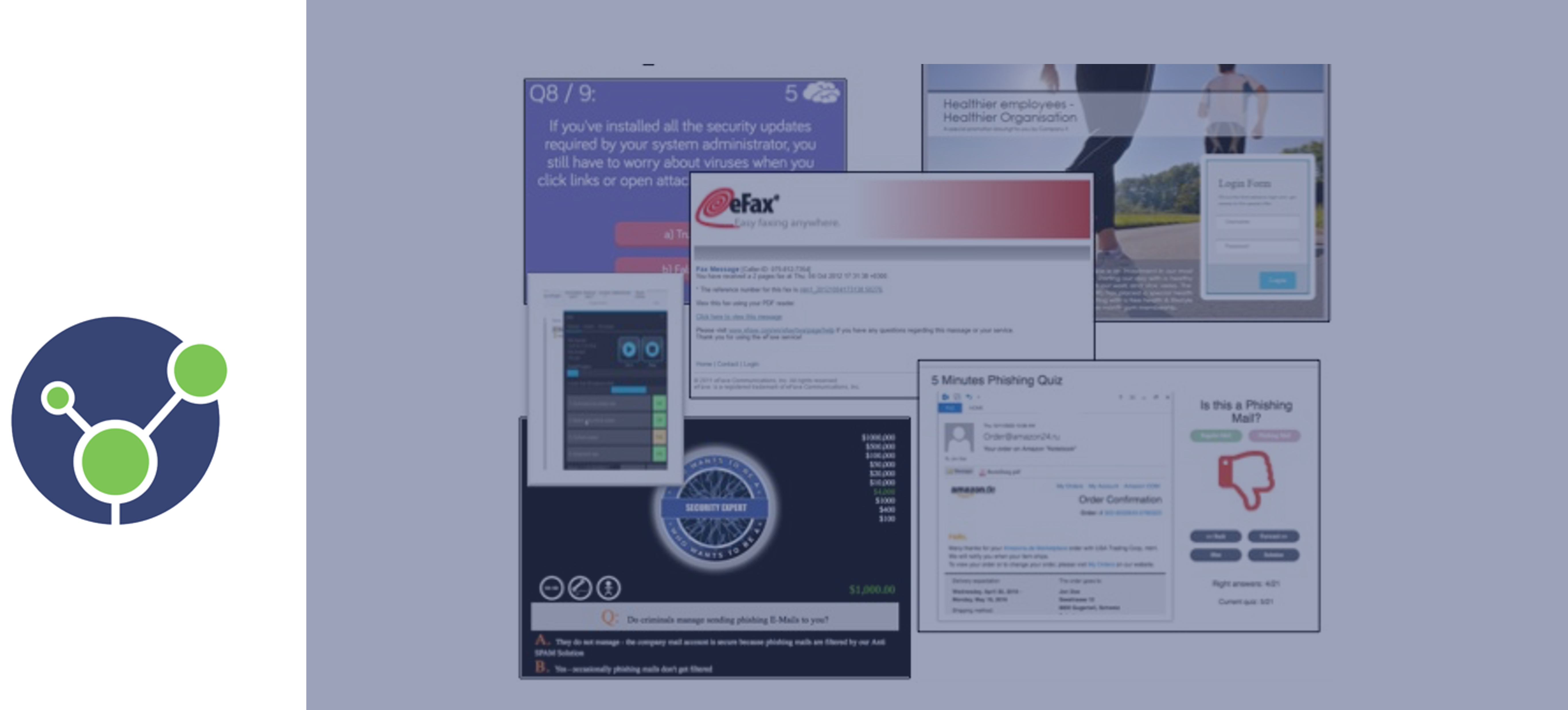
34 steps to the perfect phishing simulation
Everything you need for a successful implementation of an phishing attack simulation and an awareness training. According to our experience, phishing simulations provide a higher ROI compared to more traditional cybersecurity training methods. Employees remain the most attacked vector by the cyber criminals. And your users cannot be trained overnight, so this endeavor will require[…]